Our digital world unfolds like a story, with every cyber threat contributing a plot twist. As we step
into 2024, several trends and threats are shaping the way we approach digital security. Let us
explore them in this blog, one by one.
Generative AI – A Double-Edged Sword
Generative AI, with its ability to create diverse content, brings both promise and risks to the realm
of cybersecurity. It fuels the creation of misinformation, spam, and biased outcomes, posing
significant threats to individual privacy and public trust. Cybercriminals can use fabricated content
to tarnish reputations or even trigger conflicts.
However, on the flip side, generative AI has the potential to enhance cybersecurity.
We can use generative AI to detect threats, conduct vulnerability assessments, and even create
effective cybersecurity training modules. Organizations can proactively leverage generative AI to
identify and mitigate cybersecurity risks, paving the way for advanced digital defense.
The AI-Enhanced Phishing Threat
Phishing attacks are evolving into sophisticated threats backed by Artificial Intelligence.
Cybercriminals now use AI to automate the creation of convincing emails, generate fake websites,
and identify potential victims with alarming accuracy.
Navigating this landscape requires a combination of user caution and robust security practices.
➢ Be vigilant when you receive unsolicited emails.
➢ Avoid clicking on unfamiliar links or attachments.
➢ Verify URLs, use strong passwords and two-factor authentication, and
➢ Keep security software up to date.
By adopting these practices, individuals can minimize the risk of falling prey to AI-driven phishing
attempts.
Cyber Resilience vs. Cybersecurity
While cybersecurity focuses on proactive measures to safeguard systems, networks, and programs,
cyber resilience refers to an organization’s ability to endure and recover from cyberattacks.
In the digital age, these two approaches collaborate to offer wholesome protection against
cyberattacks.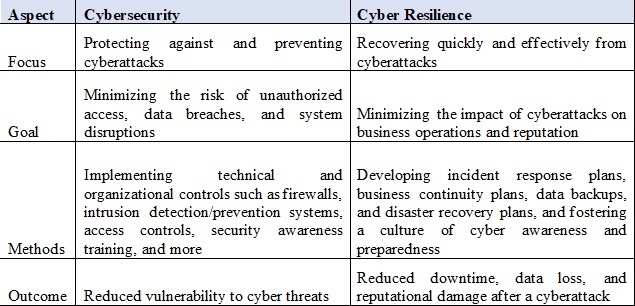
Zero Trust: A Paradigm Shift
The zero-trust security model emerges as older security methods struggle against
more advanced cyber threats. With a strong emphasis on checking user and device identities before
allowing access, zero trust helps lower the chance of cyberattacks, especially with the increase in
remote work.
Putting this model into action requires a well-thought-out plan, solid identity, and access
management, dividing networks into segments, and keeping a constant watch. By doing this,
organizations strengthen their defenses, making sure only authorized users get to resources,
boosting security in today’s fast-paced digital world.
Mitigating Security Fatigue with Zero Trust
When users have an overwhelming number of security decisions to make, they might end up
ignoring warnings, reusing passwords, and falling victim to phishing attempts.
Some of the primary reasons for security fatigue could be:
➢ Constant Exposure to Warnings
➢ Overly Complex Security Procedures
➢ Lack of Training and Awareness
How can Zero Trust Help?
➢ Zero Trust’s Single Sign-On feature avoids password fatigue.
➢ Simple access management with Least Privilege Access helps both users and IT.
➢ Continuous verification reduces the fatigue caused by security alerts.
➢ Secure access brings efficiency and empowerment, reducing user stress.
➢ Zero Trust focuses on real risks, optimizing resources, and easing strain.
➢ The iterative approach facilitates continuous improvement.
➢ User-friendly access and empowerment enhance the overall user experience.
➢ Better security with Zero Trust minimizes stress from threats.
Countering Deepfakes: A Collective Effort
Deepfakes refer to videos or audio recordings that seem realistic but are fake. For instance, one
can create a video of you saying something controversial, without you doing it in reality. In the
hands of the wrong people, deep fakes can be destructive for individuals as well as society as a
whole.
Machine learning advancements can improve deepfake detection technology. Meanwhile,
individuals should be more aware and develop enough knowledge to differentiate fabricated
content from real ones. Social media platforms can prioritize transparency and accountability by
clearly labeling suspected deepfakes and providing authentic information.
To tackle the risks of deep fakes, everyone—people, tech companies, policymakers, and
researchers—should work together.
Conclusion:
Navigating the future of cybersecurity in 2024 requires a multifaceted approach that embraces both
the challenges and opportunities presented by emerging technologies. To create a safe digital
future, let’s stay informed, follow best practices, and work together for collective digital security

Cyber Security
Biometric Authentication: Revolutionizing IAM Security
Security defenses that rely heavily on passwords are no longer enough to safeguard us. In fact, they are leaving us more vulnerable to attacks. Cybercriminals

