IAM Rollout: Best-in-Class Practices
In the realm of digital security, Identity and Access Management (IAM) stands as the gatekeeper, determining who has access to what, and when. Similar to an adept traffic controller navigating a busy intersection, IAM expertly directs the flow of users into specific digital pathways.
With careful management, Identity and Access Management secures the digital privacy of your business by
🔹Overseeing user information.
🔹Governing access to digital resources.
🔹Guaranteeing a secure work environment.
In a world grappling with escalating cyber threats, remote work dynamics, and stringent data privacy regulations, IAM has transcended from a mere IT convenience to a pivotal security and compliance necessity.
IAM’s role is foundational in protecting data, ensuring accountability, and upholding security across the vast expanse of today’s digital landscape. As organizations face a rising tide of data breaches, with 34% of victims experiencing identity theft subsequently, the implementation of robust IAM practices becomes paramount.
Embracing Advanced IAM Practices
In the pursuit of a secure digital ecosystem, it becomes imperative to go beyond conventional IAM approaches. Adopting advanced practices is not just a choice but a necessity. The advanced IAM practices include:
🔹Machine Identities with Least Privilege and Zero Trust
🔹Advanced Multi-Factor Authentication (MFA)
🔹Decentralized Identity Paradigm
🔹Integration of AI and MI Technologies
🔹Emphasis on User Consent and Data Privacy
MetroMax’s Approach to IAM Rollout
Our approach is a comprehensive journey from envisioning future landscapes to smooth end-to-end implementation. We meticulously assess and enhance IAM strategies, ensuring a secure and adaptive framework. Our commitment extends to flawless roll-outs, from preparing prerequisites to executing strategic blueprints, conducting rigorous testing, and facilitating smooth transitions. Upholding best practices, we forge a secure IAM framework, providing users with an exemplary digital experience.

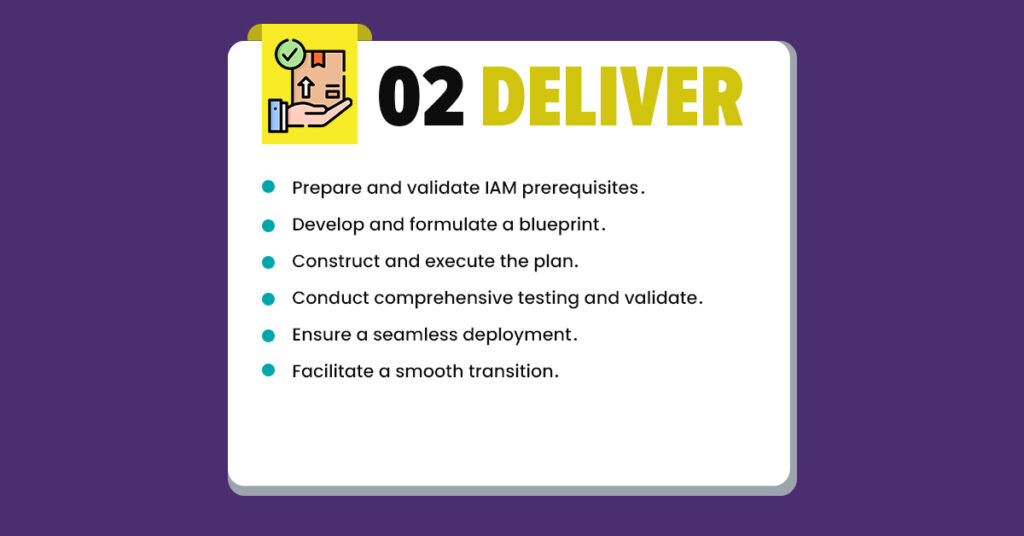

(To learn about our rollout approach in detail, download our latest thought paper on IAM-Roll-Out-Best-Practices)
Implementing Zero Trust: A Crucial Milestone
As we traverse the digital landscape, the implementation of a zero-trust approach emerges as a crucial milestone. With over 1.3 billion records compromised due to data breaches in 2022, the principles of least privilege (PoLP) become indispensable.
(To delve deep into the impact of data breaches, read our blog on ‘The Rising Cost of Data Breaches – 2023’)
The Principle of Least Privilege (PoLP)

Conclusion: Fortifying Your Digital Future
In conclusion, implementing the best IAM rollout practices has become a strategic necessity, and at MetroMax, we lead the way in effective and advanced IAM implementation. By embracing our carefully crafted IAM practices, organizations can bolster their defenses against evolving cyber threats with confidence.
In partnership with Saviynt Solutions, our approach involves not only adopting top-tier IAM technologies but also customizing them to suit the specific needs of our clients. The MetroMax IAM roadmap adapts to the ever-changing digital landscape, ensuring resilience and adaptability. Through our steadfast commitment to the principles of least privilege, user consent, and stringent data privacy, MetroMax establishes a standard for a secure digital future.
With MetroMax, your organization can confidently step into a future where IAM is masterfully orchestrated for enduring security and trust.


