October 01, 2021 – Johnson Memorial Health, Indiana, encountered a ransomware attack, the consequences of which still give them nightmares. The hackers had left a ransom note on every server demanding $3 million in Bitcoin.
Suddenly, the world has turned upside down for the hospital staff. They had to resort to pen and paper to prepare medical records. The hospital was in a very tricky situation. If they paid the ransom, the government might impose fines for initiating payments to cybercriminals. If they do not pay the ransom, the attackers might leak sensitive patient data, causing them cybersecurity regulation and compliance issues. Above all, the hospital was overflowing with patients seeking health care.
The hospital decided not to pay, disconnected all systems including the critical ones to prevent further invasion, and diverted emergency cases to other hospitals. Nurses had to guard newborn babies round the clock, and the fetal monitors shut down, affecting laboring women. The staff described the experience as worse than that of COVID! Moreover, the hospital is still recovering from the damages caused by the attack.
The Importance of Cybersecurity in Healthcare Sector:
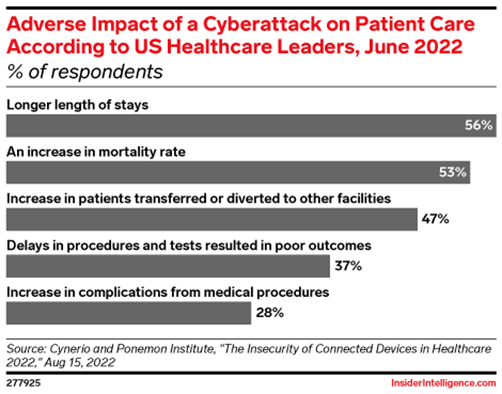
Image Source: InsiderIntelligence.com
The healthcare sector is increasingly becoming a primary target for cyberattacks because they collect and store sensitive data like names, addresses, Social Security Numbers, and medical records. Let us look at the reasons why cyber attackers target the healthcare industry.
- There are many regulations such as the Health Insurance Portability and Accountability Act (HIPAA) of 1996, governing the healthcare sector to protect patient data. The consequences of a data breach would be severe, which becomes an advantage for cyber attackers.
- Ironically, healthcare organizations do not have advanced cybersecurity systems to protect patient records.
- The impact of a cyberattack is more severe for healthcare organizations, as apart from financial losses and reputational damage, cyberattacks can disrupt patient health care. Hence, cyberattackers see hospitals as easy targets for demanding ransoms.
How do cyberattackers misuse stolen data?
Identity theft: Cybercriminals use the stolen information to open bank accounts, apply for loans, or even take out credit cards in the victim’s name.
Medical fraud: Cybercriminals can fraudulently bill insurance companies for services that were never rendered or submit false claims.
Blackmail for Ransom: As the healthcare sector is highly regulated, Cybercriminals threaten to release stolen healthcare data if the victim does not pay a ransom.
Data extortion: Cybercriminals can sell or trade stolen healthcare data on the dark web, which can be used for malicious purposes, such as identity theft, medical fraud, or insurance fraud.
Disruption of healthcare services: Cybercriminals can disrupt healthcare services by shutting down hospital systems, leaking patient information, or launching DDoS attacks. Such activities can be part of cyberterrorism to instill fear or intimidate the society.
How to Protect Patient Data?
Ø Educate hospital staff on cybersecurity best practices. This includes teaching them about phishing scams, malware, and other threats. Furthermore, train them on how to use the organization’s security policies and procedures.
Ø Restrict access to patient data. Only authorized personnel should have access to patient data. This restriction can be achieved through Role-Based Access Control (RBAC), which allows administrators to define who can access what data and what actions they can take.
Ø Use strong passwords and Multi-Factor Authentication (MFA). To enhance security, it is advisable to use passwords that consist of a minimum of 12 characters, incorporating a combination of both uppercase and lowercase letters, numbers, and symbols. Multi-factor authentication (MFA) enhances security by requesting users to input a code from their mobile device alongside their password, introducing an additional layer of protection.
Ø Encrypt patient data. Encryption involves transforming data into a format that remains unreadable without the necessary key for decryption. This makes it much more difficult for unauthorized users to access patient data. It should be encrypted both when stored and transferred.
Ø Monitor and audit systems. Organizations should monitor their systems for suspicious activity and regularly audit their security logs to identify any potential breaches.
Ø Keep software up to date. Software vendors often release security patches to fix vulnerabilities. Organizations should proactively install these patches to protect their systems from attack.
Ø Have an incident response plan in place. In the event of a data breach, organizations should have a plan to recover their data and restore operations.
Ø Ensure third-party vendors who handle critical data adhere to the cybersecurity standards.


