In this digital age, the stage is all set for Small and Medium-sized Businesses (SMBs) to showcase their innovation online. However, it is a well-known fact that cyber threats prey on unsuspecting SMBs that do not have a secure infrastructure.
According to Forbes, small businesses are three times more likely to be targeted by cybercriminals than larger companies.
The Cybersecurity Concerns of SMBs
Small and Midsize Businesses are the heart of our economy. They drive innovation and contribute significantly to local communities. However, they are also easy targets for cybercrimes due to limited resources and a lack of advanced cybersecurity solutions.
With cyber risks growing exponentially, a robust IAM solution is essential to protect digital assets from cyberattacks.
The Importance of IAM Solutions
Identity and Access Management (IAM) keeps businesses safe from cyber threats and ensures only the right people can access important information and systems. These solutions help SMBs lower the chances of data breaches, insider attacks, and other cyber problems. Now, let’s explore the different components of a robust IAM system.
There are four main components of Identity and Access Management:
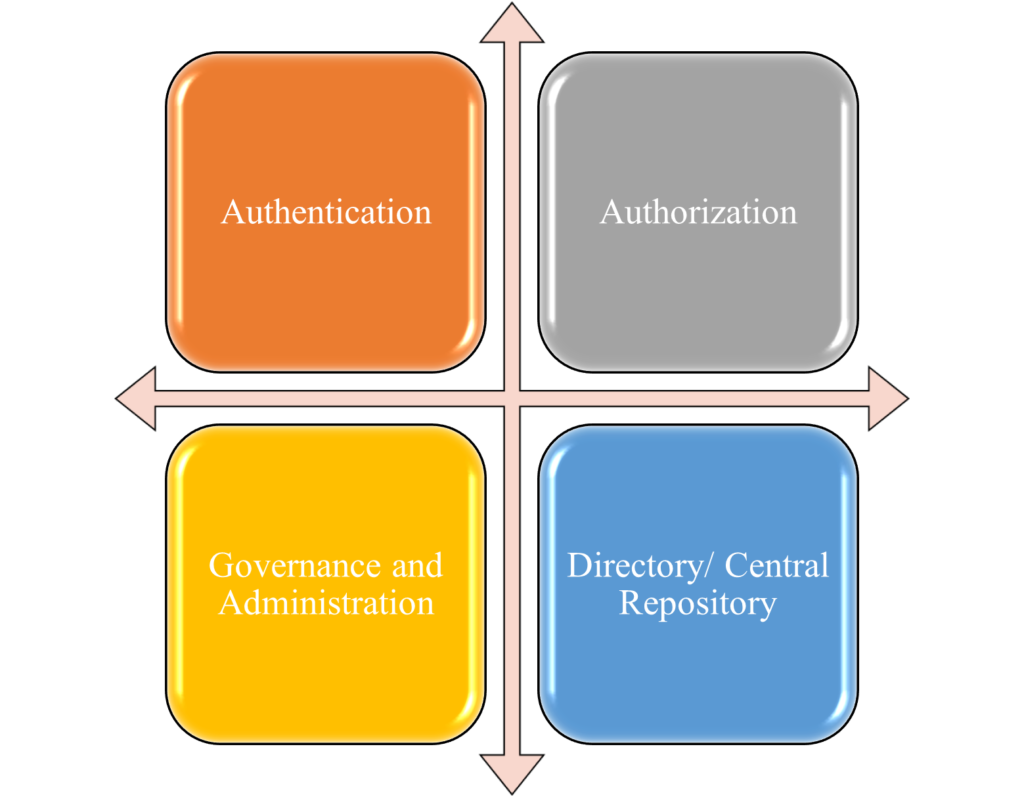
Authentication:
Authentication is a critical process that verifies the identity of a user before granting access to computer systems. It ensures that only authorized individuals gain entry. It enhances overall security and protects digital assets against cyber threats. There are several methods to verify identity:
- Password-based authentication
- Multi-Factor Authentication (MFA)
- Biometric authentication
- Single Sign-On (SSO)
- Certificate-based authentication
- Token-based authentication
- Knowledge-based authentication
- Smart card authentication
Authorization:
Authorization determines whether users should be allowed access to specific resources or actions based on their identities and permissions. It ensures secure access to sensitive information and helps maintain control over the organization’s resources. There are different ways to manage access control:
- Resource Access Control
- Role-Based Access Control (RBAC)
- Attribute-Based Access Control (ABAC)
- Least Privilege
- Access Revocation
- Fine-Grained Access Control
- Dynamic Authorization
Governance and Administration:
Identity Governance and Administration (IGA) in IAM set up rules and procedures to manage who can access important information and systems in a company or organization. The main goal is to maintain a safe and organized environment.
It helps the company control access privileges for compliance with regulations and keeps the infrastructure secure. This way, the company can run smoothly and protect itself from cyberattacks. The main aspects of Governance and Administration are listed below.
- Identity Lifecycle Management
- Access Governance
- User Provisioning
- Role Management
- Access Certification
- Audit and Compliance Reporting
- Policy Enforcement
Directory/Central Repository:
The directory/Central Repository in IAM keeps track of all the crucial information about users, groups, and their permissions in a company or organization. It’s like a well-organized file system that provides information on every user.
Directory helps the company find and manage user details quickly and efficiently. It also connects with other systems within the organization to keep everything in sync and ensure consistency in data across systems. Moreover, it has security measures to keep the information safe and accessible to authorized users only.
Listed below are the main components of the directory.
- User Identity Records
- Directory Schema
- Directory Search
- Directory Integration
- Directory Replication
- Directory Security
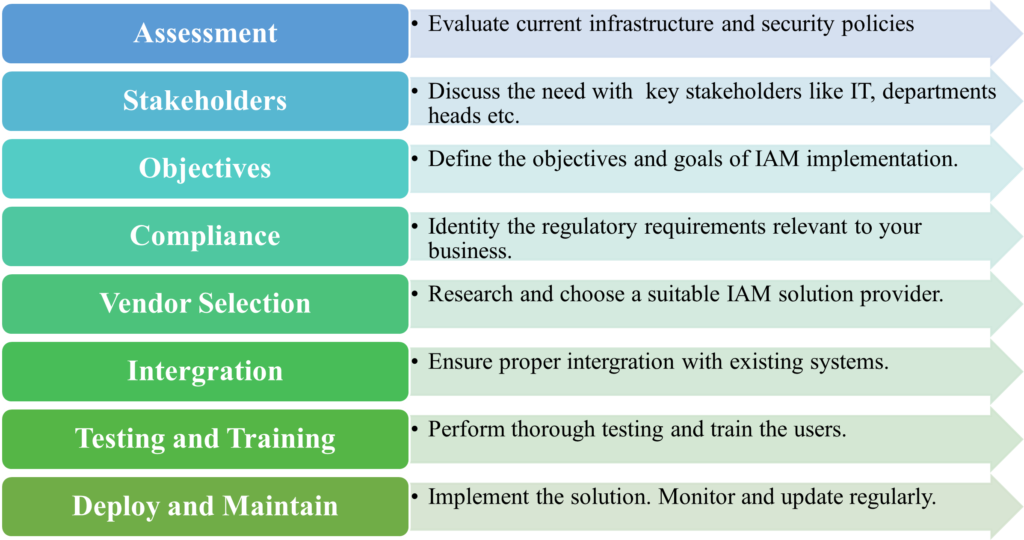
The Eight-Step Process of IAM Implementation
MetroMax Solutions – Your Trusted IAM Solutions Provider
At MetroMax, we are committed to helping SMBs secure their digital future. Our team of IAM experts is ready to partner with your business, offering personalized and cost-effective IAM strategies that cater to your unique needs.
Book your FREE Consultation today!


