“Multifactor authentication is the seatbelt of cybersecurity. It may take a little extra effort, but it greatly reduces the risk of a devastating breach.” – Stu Sjouwerman
In the digital world, where data theft and cyberattacks are becoming more common, businesses need strong security measures to protect their digital assets and sensitive information. One effective tactic against cyberattacks is called Multifactor Authentication (MFA). MFA adds an extra layer of security to reduce the risks associated with using just passwords.
Passwords: The Weak Link in Cybersecurity
Think of a password as a lock on a front door. A single lock may be enough for a small house but imagine a big castle with many entrances and exits. Would one lock be enough? To protect the castle, they build a moat, install a strong gate, have guards at all entrances, and set up watchtowers to spot anything suspicious. They have multiple layers of protection.
Similarly, passwords are commonly used for security, but they are easily attacked, through phishing or credential stuffing. Multifactor Authentication combines passwords with other security measures to make things safer.
How does Multifactor Authentication (MFA) Work?
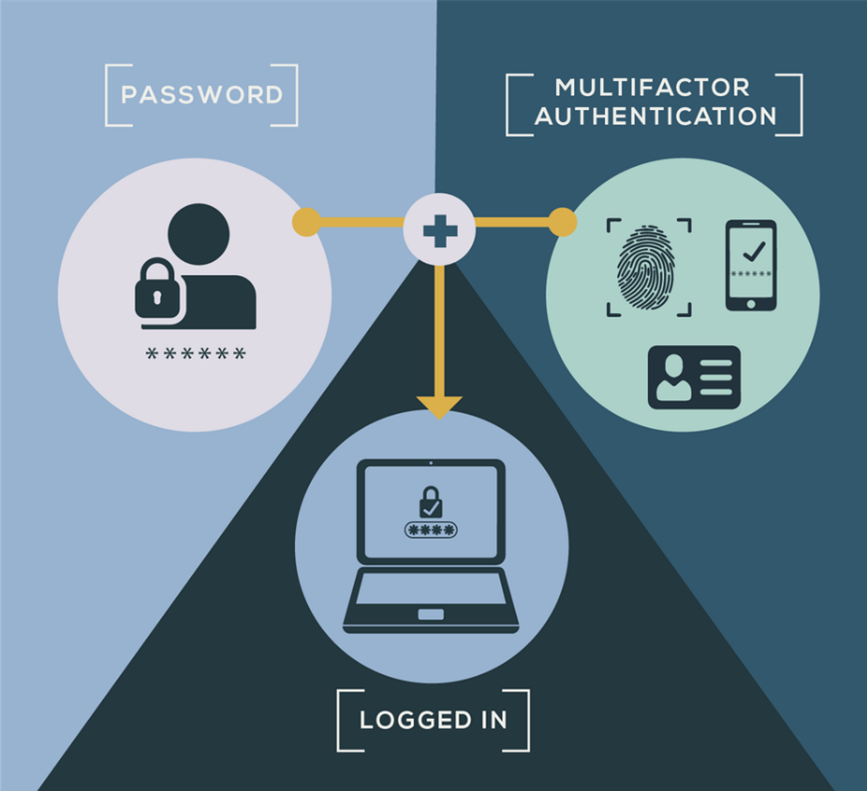
MFA provides an additional layer of protection to reduce the risk of unauthorized access. It requires users to prove their identity with multiple factors. By combining passwords with other security measures, MFA makes things much safer.
The benefits of MFA are:
- Enhanced Security
- Improved User Experience
- Compliance with Data Protection Regulations
- Flexible and Compatible with Existing Systems
Let us take a look at the factors MFA incorporates for additional security.
Passwords: A traditional but essential factor, passwords are made strong through complex rules and regular updates.
One-Time Passwords (OTP): Temporary codes that are sent through SMS, email, or authenticator apps. They are valid for a brief time and can’t be used again, adding extra security.
Biometric Authentication: This uses unique physical or behavioral characteristics, like fingerprints or facial recognition, to make sure it’s really you. It’s very secure because it’s hard to replicate.
Hardware Tokens: Physical devices like smart cards or USB keys add an extra layer of protection. They generate one-time passwords or store digital certificates, giving secure access to corporate systems.
Contextual Factors: This means checking information like the user’s location, device details, or behavior patterns to assess how risky the situation is. For example, if someone tries to log in from an unknown place, extra authentication steps will be needed to ensure safety.
According to Microsoft, MFA prevents 99.9% of automated attacks on its platforms’ websites and other online services. (Source: llcbuddy.com)
Google claims that adding a recovery phone number to your Google Account may stop up to 100% of automated bots, 66% of targeted attacks, and 99% of bulk phishing assaults (Source: llcbuddy.com)
The Rising Trend of Passwordless Authentication
As passwords are seen as a weak link in security, passwordless authentication methods are gaining popularity in corporates. By relying less on passwords, organizations can enhance security and streamline the user experience. These methods use alternative factors for identity verification.
Biometric authentication: Using physical traits like fingerprints or facial recognition for a secure login experience.
Public Key Cryptography – FIDO2 (Fast Identity Online 2.0) and WebAuthn (Web Authentication) standards enable users to authenticate using cryptographic keys instead of passwords. Hardware security keys and built-in authenticators help build a secure passwordless authentication framework.
How to Implement MFA?
As corporate cybersecurity threats evolve, robust multifactor authentication is essential for every organization. As a leading provider of Identity and Access Management solutions, MetroMax Solutions can help you can help analyze your security needs, assess your current systems, and provide a scalable solution to protect your digital assets from cyberattacks.
To learn more about our range of solutions and services, book your FREE consultation with our experts today.


